Large parts of our business community here in North Florida are now embracing the idea of a mobile workforce to help stop the spread of the Coronavirus. We are seeing the utilization and deployment of cloud solutions (Dropbox, 365 Google Drive), remote and secure connectivity solutions (VPN), collaborative apps (Teams, Sharepoint), and other communication tools (Zoom, Slack) to keep the engines of our economy running. We are also seeing the criminal element, especially hackers coming up with new and devious tactics using the coronavirus as the theme. For example, there are phishing emails going out now claiming to be from the World Health Organization that when opened, install malware on your computer. There are fake maps of exposed areas that when you visit their site you are exposed to malware also. There are even malicious texts going around from hackers like the one below. Do not click or your phone will be in most cases compromised in some fashion. There are even instances of criminals offering “cures” and treatments for the virus that are also fraudulent.
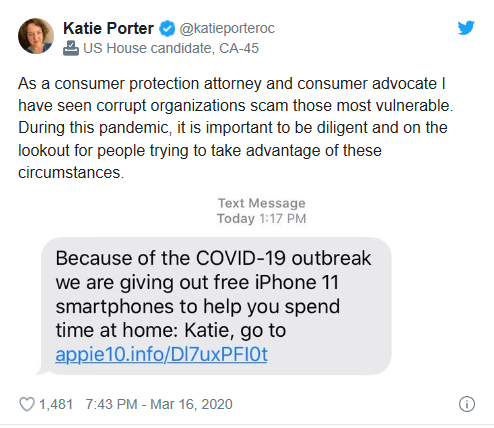
As this situation continues, please educate your staff and teams to be on the look-out for these types of threats as we will see more and more of this in the coming days and weeks. Stay safe and if you have any questions or concerns let me know.
More info here in an article
More info here in a video
Blake Dowling is CEO of Aegis Business Technologies. He is also the host of the Biz and Tech Podcast and writes technology and business columns for several organizations. He can be reached here: dowlingb@aegisbiztech.com

